
Let us also get some Perception from one of The key implementations on the planet. As we will see, it actually matches out idea flawlessly!
Programmers have a singular method of resolving difficulties. Explore what that programmer mentality is about.
Hashing in cybersecurity calls for unidirectional procedures that make use of a just one-way hashing algorithm. It truly is a vital step in stopping menace actors from reverse engineering a hash back to its original state.
Non-reversible. Since hash capabilities are meant to be just one-way functions, reversing the method and getting the original enter facts is not computationally practical. This might be a drawback if reverse lookup is necessary.
The dampness present within the flower, Dry Sift, or ice water hash will build steam strain and power the oil from the source creating a solventless hash product.[34]
Hashish is often a cannabis concentrate product made up of compressed or purified preparations of stalked resin glands, named trichomes, from the plant. It really is described from the 1961 UN Solitary Conference on Narcotic Medications (Timetable I and IV) as "the divided resin, irrespective of whether crude or purified, attained from the cannabis plant". The resin contains substances for instance tetrahydrocannabinol (THC) along with other cannabinoids—but usually in higher concentrations than the unsifted or unprocessed cannabis flower.
The indoor established, on Stage 09 at Fox Studios in Century Metropolis, was employed for the indoor scenes for your run with the collection. Later, after the indoor set was renovated to permit most of the "outdoor" scenes to become filmed there, both of those sets have been used for exterior taking pictures as script prerequisites dictated (e.g., night time scenes were significantly simpler to film about the audio phase, but scenes with the helicopter pad demanded using the ranch).
Hash output. Unlike the input, the hashing procedure's output or hash benefit contains a established duration. It is complicated to ascertain the duration of the original enter mainly because outputs have a established length, which contributes to an Total Enhance in protection.
For those who’re pursuing a vocation in cybersecurity, you’ll will need to comprehend hashing’s job in information protection, integrity, and privacy. It’s also a worthwhile tool for Back-Conclude Engineers and Information Experts.
When someone generates and encrypts a digital signature with a private critical, hash details is also developed and encrypted. The signer's public crucial then permits the recipient to decrypt the signature.
At present, it is acceptable to tag only considerable posts that will add to the overall dialogue with a single hashtag. Using two hashtags is acceptable, especially when on the list of # tags includes an genuine location, for example #SanDiego and #wildfires. In line with Wikihow, using 3 hashtags in a single Tweet is absolutely the optimum, and doing this hazards "increasing the ire from the Local community."
6M) will invent new microscopes and various tools to determine microscopic more info cancer remnants inside the affected person to help the surgeon remove all remaining cancer cells ahead of the close of the treatment.
Hashing is the entire process of reworking any presented vital or a string of people into another benefit. This is generally represented by a shorter, set-size value or crucial that represents and makes it much easier to uncover or make use of the original string.
The first attestation on the time period "hashish" is inside of a pamphlet revealed in Cairo in 1123 CE, accusing Nizari Muslims of staying "hashish-eaters".[fourteen] The cult of Nizari militants which emerged after the fall of your Fatimid Caliphate is commonly called the sect of your Assassins—a corruption of hashishin, Arabic for "hashish-smokers.
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now! Jennifer Grey Then & Now!
Jennifer Grey Then & Now!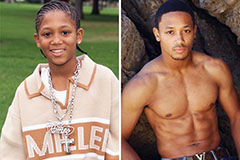 Romeo Miller Then & Now!
Romeo Miller Then & Now! Michelle Trachtenberg Then & Now!
Michelle Trachtenberg Then & Now! Bill Cosby Then & Now!
Bill Cosby Then & Now!